Researchers at QuTech in Delft have succeeded in teleporting quantum information across a rudimentary network. This first of its kind is an important step towards a future quantum internet. This breakthrough was made possible by a greatly improved quantum memory and enhanced quality of the quantum links between the three nodes of the network.
The nodes of such a quantum network consist of small quantum processors. Sending quantum information between these processors is no easy feat. One possibility is to send qubits using light particles but, due to the inevitable losses in glass fibre cables, in particular over long distances, the light particles will very likely not reach their destination. As it is fundamentally impossible to simply copy qubits, the loss of a light particle means that the quantum information is irrecoverably lost.
Teleportation offers a better way of sending quantum information. The protocol for quantum teleportation owes its name to similarities with teleportation in science-fiction films: the qubit disappears on the side of the sender and appears on the side of the receiver. As the qubit therefore does not need to travel across the intervening space, there is no chance that it will be lost. This makes quantum teleportation an crucial technique for a future quantum Internet.
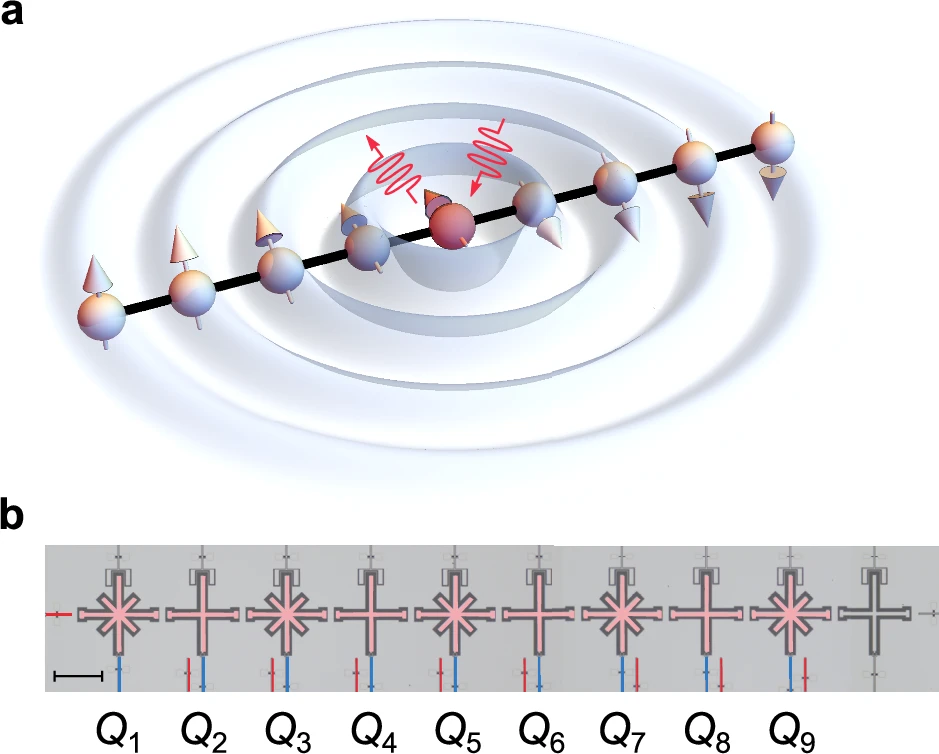
In order to be able to teleport quantum bits, several ingredients are required: a quantum entangled link between the sender and receiver, a reliable method for reading out quantum processors, and the capacity to temporarily store quantum bits. Previous research at QuTech demonstrated that it is possible to teleport quantum bits between two adjacent nodes. The researchers at QuTech have now shown for the first time that they can meet the package of requirements and have demonstrated teleportation between non–adjacent nodes, in other words over a network. They teleported quantum bits from node “Charlie” to node “Alice”, with the help of an intermediate node “Bob”.
The teleportation consists of three steps. First, the “teleporter” has to be prepared, which means that an entangled state must be created between Alice and Charlie. Alice and Charlie have no direct physical connection, but they are both directly connected to Bob. For this, Alice and Bob create an entangled state between their processors. Bob then stores his part of the entangled state. Next, Bob creates an entangled state with Charlie. A quantum mechanical “sleight of hand” is then performed: by carrying out a special measurement in his processor, Bob sends the entanglement on as it were. Results: Alice and Charlie are now entangled, and the teleporter is ready to be used!
The second step is creating the “message” — the qubit — to be teleported. This can, for example, be ‘1’ or ‘0’ or various other intermediate quantum values. Charlie prepares this quantum information. To show that the teleportation works generically, the researchers repeated the entire experiment for various qubit values.
Step three is the actual teleportation from Charlie to Alice. For that purpose, Charlie carries out a joint measurement with the message on his quantum processor and on his half of the entangled state (Alice has the other half). What then happens is something that is possible only in the quantum world: as a result of this measurement, the information disappears on Charlie’s side and immediately appears on Alice’s side.
You might think that everything is then completed, but nothing could be further from the truth. In fact, the qubit has been encrypted upon transfer; the key is determined by Charlie’s measurement result. So Charlie sends the measurement result to Alice, after which Alice carries out the relevant quantum operation for decrypting the qubit. For example via a “bit flip”: 0 becomes 1 and 1 becomes 0. After Alice has carried out the correct operation, the quantum information is suitable for further use. The teleportation has succeeded!
The paper has been published in Nature.