A recently published patent (https://www.ipo.gov.uk/p-ipsum/Case/PublicationNumber/GB2590064) has claimed the development of a novel quantum key distribution protocol purporting to achieve long-range quantum security without trusted nodes and without use of quantum repeaters.
This document analyzes these claims made in the ARQ19 patent regarding a novel Quantum Key Distribution (QKD) protocol that purportedly achieves long-range quantum security without trusted nodes or quantum repeaters. The analysis concludes that these claims are largely unfounded.
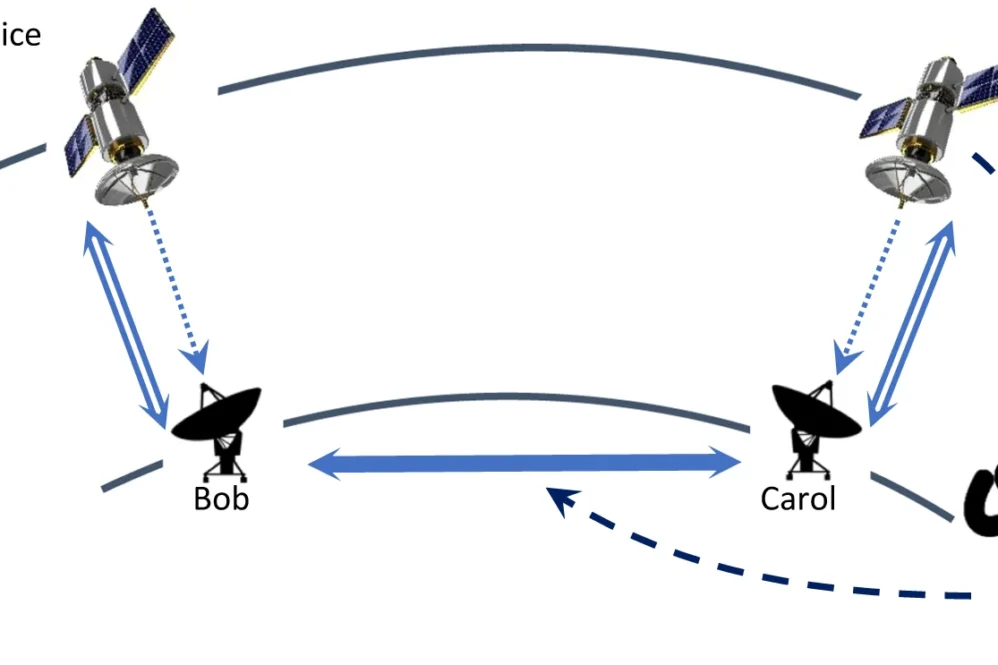
The ARQ19 protocol works as follows: First, Bob exchanges quantum objects with a satellite (Alice) but doesn’t fully process them to get a secret key. Alice gets a raw key while Bob has a sifted key. Later, Carol performs the same exchange with the satellite. Alice then creates an XOR of the two raw keys and sends it to Carol. Bob tells Carol which bits of his sifted key he kept, allowing Carol to know which bits of the XORed key to retain. Carol performs another XOR operation and tells Bob which bits she removed. This results in Bob and Carol sharing a common sifted key that requires further processing to become a secret key.
The critical flaw in this protocol lies in its requirement for a confidential discussion channel between Bob and Carol that must be kept secret from Alice (the satellite). This requirement is not minor – since an untrusted satellite could potentially broadcast key information to eavesdroppers, this confidential channel must be secure against any possible attacker. The ARQ19 patent doesn’t address how to achieve this security.
This creates a fundamental dilemma: If the satellite is trusted, Bob and Carol can achieve quantum security with standard QKD. If the satellite is untrusted, the system’s security is only as strong as the separate confidential discussion channel between Bob and Carol. Since this channel operates directly between Bob and Carol regardless of location, it cannot be based on current quantum technology. Therefore, the claim of achieving quantum security with an untrusted satellite appears unfounded.
The protocol does offer some security benefits, as an attacker would need to both hack the satellite and break the confidential discussion channel. However, the same level of security could be achieved with a standard QKD system using a simpler hybrid approach: Bob exchanges a QKD key with the satellite, Carol does the same, and then Bob locally generates a new key unknown to the satellite. The XOR of this key with the previous one is sent to Carol using the same type of confidential channel assumed in the ARQ19 protocol.
This hybrid approach requires breaking both key establishment schemes to compromise security – exactly like the ARQ19 protocol. However, since the confidential channel between ground stations cannot be quantum-based due to distance limitations, the claim that either scheme provides “Quantum Security” with untrusted satellites remains unfounded.
The analysis concludes that while the ARQ19 protocol may add a layer of security by requiring attackers to compromise multiple systems, its fundamental claims about achieving quantum security without trusted nodes are not supported by the technical details presented in the patent.
npj Quantum Information, Published online: 09 September 2022; doi:10.1038/s41534-022-00613-4