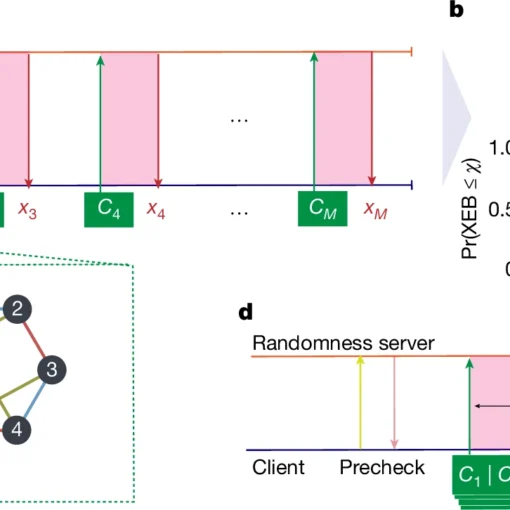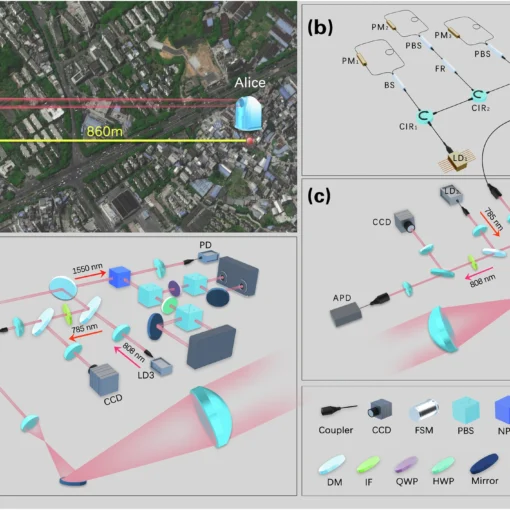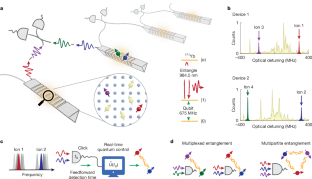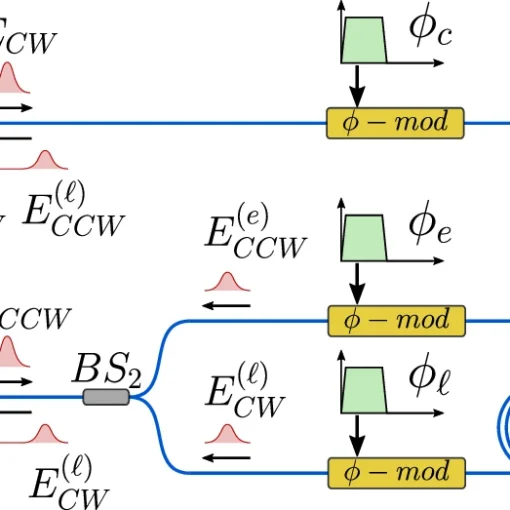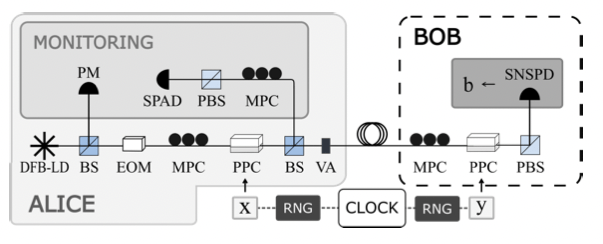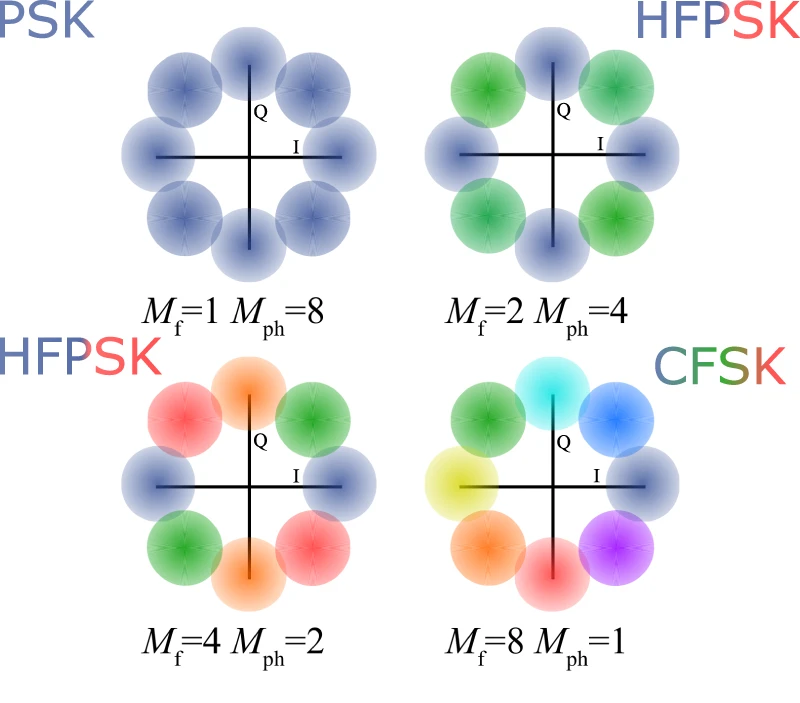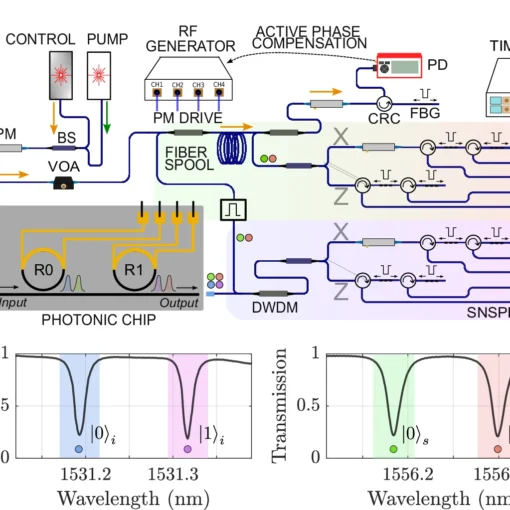
Frequency-bin entanglement-based Quantum Key Distribution
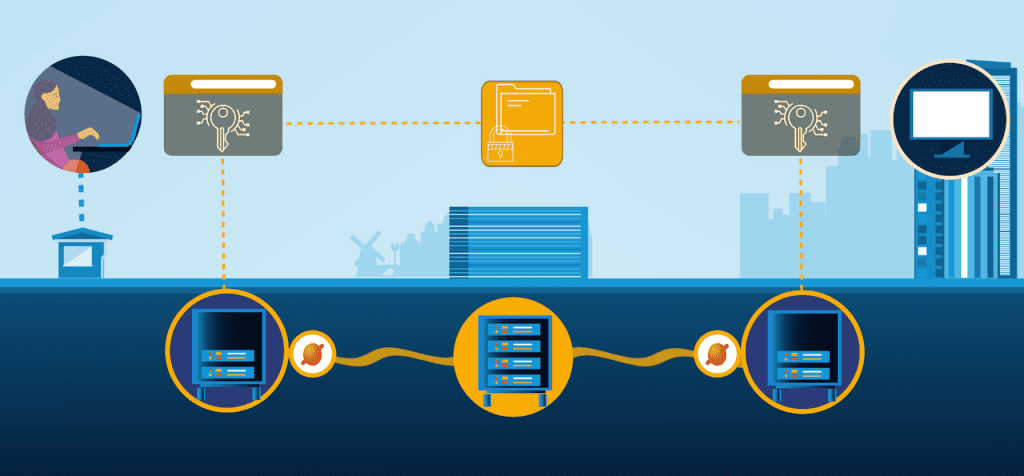
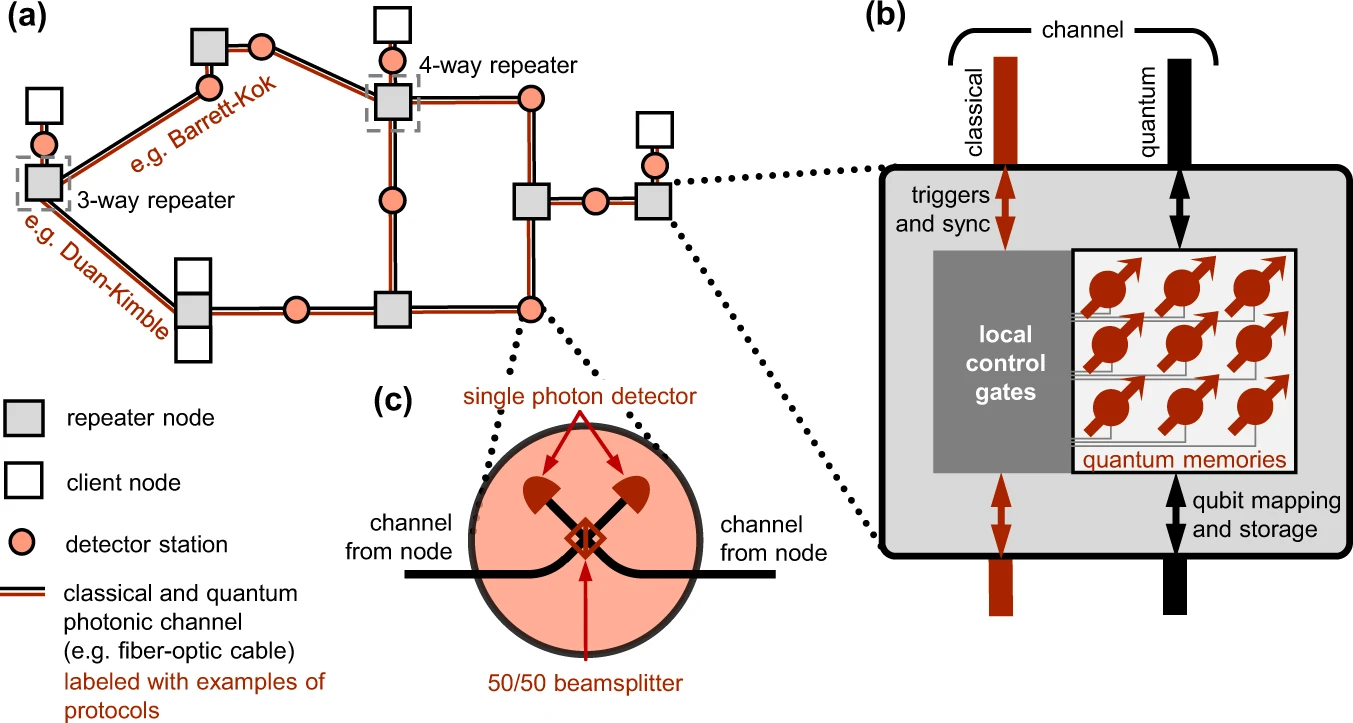
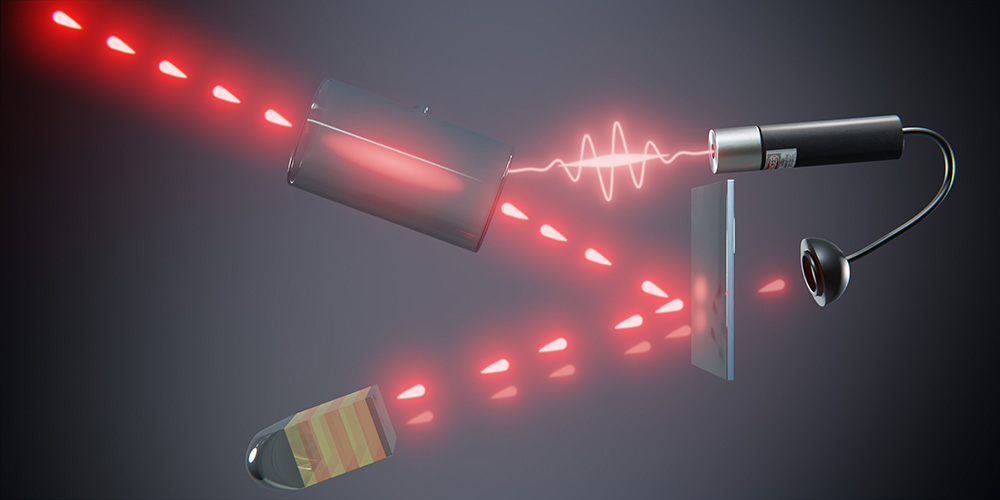
The researchers demonstrated the first complete implementation of entanglement-based quantum key distribution using frequency-bin encoding on a silicon photonic chip, overcoming phase noise challenges to achieve stable transmission over 26 kilometers of fiber with a secure key rate of at least 4.5 bits per second.