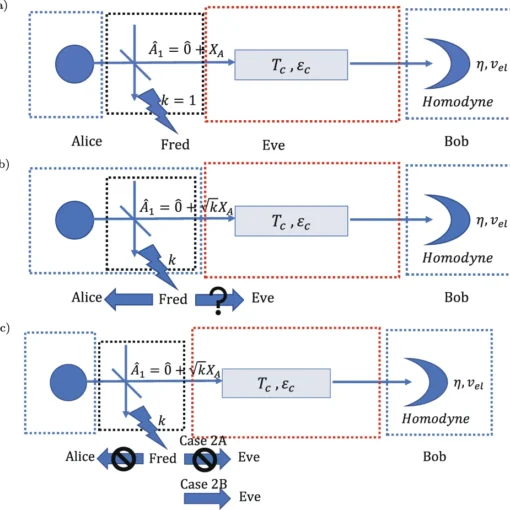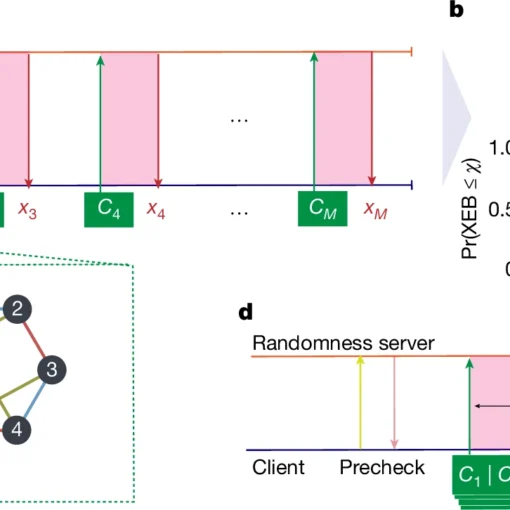
Certified randomness using a trapped-ion quantum processor
Researchers have achieved a major quantum computing breakthrough by using a 56-qubit quantum computer to generate certifiably random numbers verified by classical supercomputers, marking a shift from theoretical quantum advantage to practical application with significant implications for cryptography, security, and fairness.