Using the random orientation of the magnetization of a ferromagnetic dot after the removal of a current pulse, researchers developed a method of generating a cryptographic key for hardware security using spin-orbit torque.
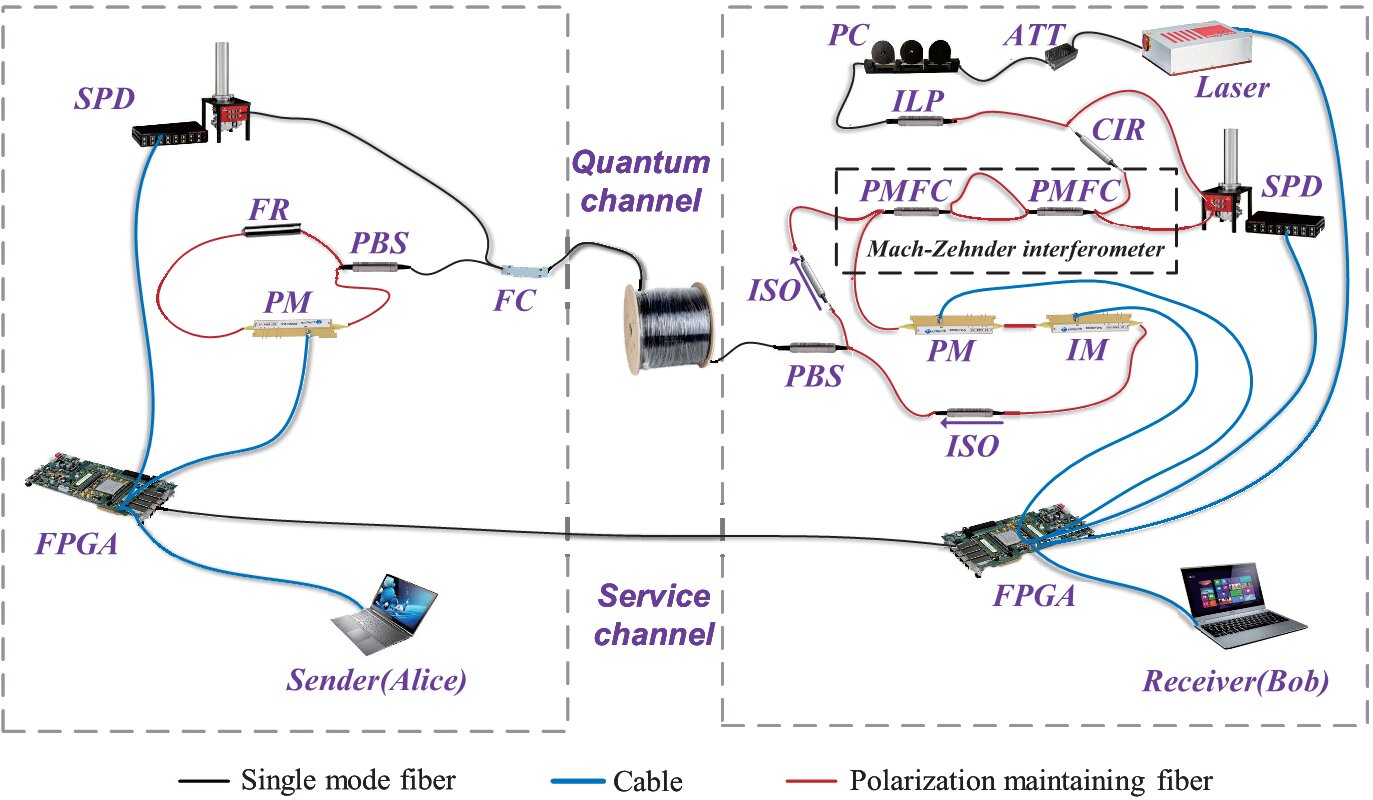
One way to achieve enhanced device security with a minimal increase in cost is using a Physical Unclonable Function (PUF), which exploits the intrinsic randomness in a process. Though PUFs typically rely on manufacturing variability, the team developed a PUF using spin-orbit torque magnetoresistive random access memory (SOT-MRAM).
By using a current pulse to induce a random positive or negative magnetic orientation in a ferromagnetic dot, the authors demonstrated a SOT-based method of generating a cryptographic key. When the pulse is removed, the magnetization in the dot relaxes into one of the two perpendicular states, which the SOT-MRAM device structure then reads.
In testing the method, the group evaluated the approach for a single dot, a composition of three dots and a 16-by-16 array of SOT-MRAM cells with consistent outcomes. They found the likelihood of a dot transitioning into either state is about 50%, regardless of its initial orientation. This is a promising result, as a 50% probability is crucial for ensuring the randomness and unpredictability.
Additionally, the prediction is robust to changes in the amplitude of the pulse, which offers a substantial advantage, due to the difficulty of ensuring a uniform field in a large array of SOT-MRAM cells. (AIP Scilight)
The research has been published in Journal of Applied Physics.